Hackers and security researchers use a method called "Google Dorking" to hunt for private data on websites. Google Dorking entails performing complex searches in Google for obscure terms, file extensions, or website attributes. You can also create a one-of-a-kind dork by putting your own spin on standard tropes. While Google Dorking has its legitimate uses, such as discovering where a website might have security holes, it is also frequently used maliciously by hackers to uncover credentials. Webmasters should take precautions to prevent unauthorized access to their sites and should not include sensitive data in directories that are searchable by the general public. Google Dorking, sometimes known as Google hacking, is the practice of exploiting Google's search features to gain unauthorized access to sites or to locate data that is hidden from general users. Advanced operators and the combination of numerous operators are required to filter our search results to optimal efficiency.
To prevent being a victim of a cyber attack, Internet users should be wary of the information they post online and use robust, unique passwords for each of their online accounts. Google handles about 8.5 billion searches per day. Using Google, we may locate vulnerable parts of websites, such as files, scripts, and databases. Google Dorks are unique search words that can be used to find results that would otherwise be impossible to find using standard search engines.
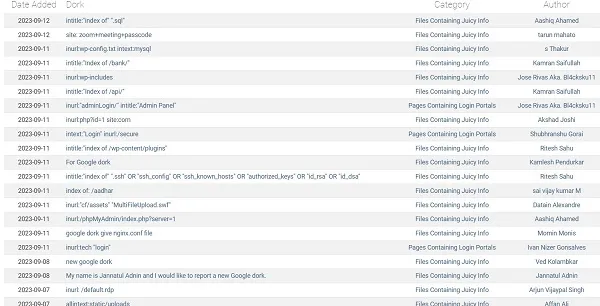
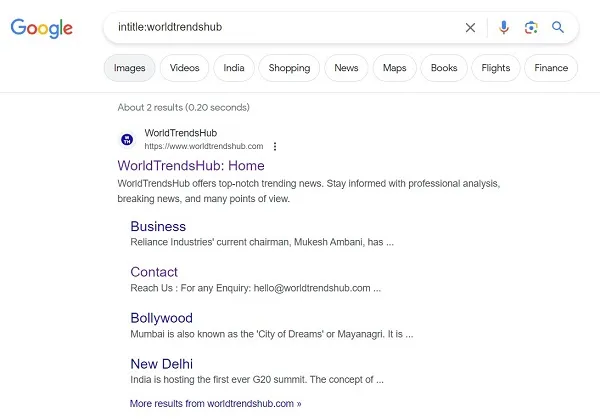
The Google Hacking Database (GHDB) is a repository of sophisticated operators and multiple-operator combinations. These nerds aren't just at Google, either. Search engines like Bing and Yahoo! can also benefit from them. Although the outcomes may be different, they all accomplish the same thing. A few examples of common operators are the pipe (|), wildcard (*), and subtract (-) operators, as well as intext, link, cache, related, filetype, site, inurl, intitle, and so on. The structure of Google Dorking query operators is very similar to that of standard Google query operators. Using these more complex operators and queries, you can get results that standard searches would never turn up.
If you use Google Dorking solely to improve your search results and not to infiltrate a company, you are unlikely to face legal consequences. Remember that Google is always monitoring your searches, and that it will label you as a threat actor if you access sensitive material or conduct a search with harmful intent. If you're looking for visual results, try looking in the Images or Videos tab. You can use a desktop image as a search query by dragging it into Google Image Search. In order to detect vulnerabilities in websites and report them to servers, several black hat hackers have deployed bots online.
Google has implemented a captcha in this procedure to put a stop to and reduce the impact of this problem. Almost every time you use a dork, you'll be prompted to submit a captcha. Google uses this method to prevent bots from abusing the search engine. The goal of this exercise is to raise awareness about the need of protecting personal information. CCTV cameras are being installed for security purposes, however these days, people don't bother to ensure that the cameras themselves are secure. By making them public, they are making matters far worse. Automated tools abound that will run a slew of Google gimmicks and save the results in text files, where you can then grep through them. Because navigating Google's many pages is the most time-consuming component of being a "Google Dork," this is helpful.
Google Dorks allows us to quickly and easily locate data and vulnerabilities that have been made public. Google Dorking is a potent strategy that can be utilized for good or evil. Website administrators and users alike should be aware of the dangers posed by the internet and take appropriate precautions. Take these precautions against Google Dorking: Password-protect files and archives containing sensitive information. Use apparatus to probe holes in online resources for data, Avoid using plaintext for storing private information and use sophisticated patterns instead. Using a robots.txt file, you may instruct search engines to avoid indexing certain parts of your website. Doing so may prevent hackers from locating vulnerable areas of your site.
Alternative methods include turning off directory indexing, installing a firewall, implementing access control and IP-based restrictions, and conducting vulnerability scans. Running your own dork queries is an excellent approach to locate any exposed component. This is so effective that some website owners actually pay for weird queries to be performed on their domain. Running queries on the entire platform and then on particular vulnerable areas can reveal if it is safe or not, but this can get complicated quickly. The time for action is afterward. Check for potentially sensitive data on your own site by running queries on it. Google Search Console allows you to remove potentially embarrassing or confidential content from search engine results.